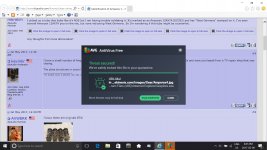
Just had four virus warnings from AVG relating to pictures in the thread "Identification of Amperex 12AX7a ECC83" in Tubes/Valves. Anyone else had problems there?
Hmm. I just installed AVG to check this (desktop OSX as well as AVG tuneup) and don't get anything. AVG does like to throw false positives to make it look like it's doing something, not that I disregard the threat or possibility of an issue in any way at all.
Bolly - were you on the "Identification of Amperex 12AX7a ECC83" page?
There are 5 images directly linked into the first page from "http://www.codekinesis.com/". This appears to be a legit (but stale and possibly compromised) website, but perhaps they got hacked. It seems normal now. AVG reports no threats on their site in the last 30 days codekinesis.com | Website Safety Report & Reviews For codekinesis.com
Google (who I personally regard with higher confidence and professionalism) says:
So... at this stage... unsure what might have caused AVG to blip. If you see this kind of thing again, please take a screenshot, save any specifics about filenames, errors, etc. Very unlikely it could have come through our Adserver, we only use Google for our ads and they do have strict rules about their ads however there have been breeches previously (that affected pretty much every site on the net).
Bolly - were you on the "Identification of Amperex 12AX7a ECC83" page?
There are 5 images directly linked into the first page from "http://www.codekinesis.com/". This appears to be a legit (but stale and possibly compromised) website, but perhaps they got hacked. It seems normal now. AVG reports no threats on their site in the last 30 days codekinesis.com | Website Safety Report & Reviews For codekinesis.com
Google (who I personally regard with higher confidence and professionalism) says:
- That thread is clean: http://www.diyaudio.com/forums/tubes-valves/307305-identification-amperex-12ax7a-ecc83.html
- 100 other scanner results say clean: https://www.virustotal.com/en/url/5...34f7747c675840f2e63d1270/analysis/1493950954/
So... at this stage... unsure what might have caused AVG to blip. If you see this kind of thing again, please take a screenshot, save any specifics about filenames, errors, etc. Very unlikely it could have come through our Adserver, we only use Google for our ads and they do have strict rules about their ads however there have been breeches previously (that affected pretty much every site on the net).
I downloaded that file individually, ran it through Virus total which uses AVG's latest virus signature database from 9th May 2017, and it tested AOK on 56 different scanners:
https://www.virustotal.com/en/file/...2212f2ad0e044f65c4f77ca8/analysis/1494377334/
I also tried it on a number of other scanners, and it comes back clean. Can you please ensure you are using today's virus signature database? Are you using the latest version of AVG?
https://www.virustotal.com/en/file/...2212f2ad0e044f65c4f77ca8/analysis/1494377334/
I also tried it on a number of other scanners, and it comes back clean. Can you please ensure you are using today's virus signature database? Are you using the latest version of AVG?
One possibility, is that as you appear to be running Internet Explorer / Windows, the webserver is compromised and it only is serving up malware to browser user agents that it can hope to infect (I use a Mac). To cater for this rare possibility, I have manually downloaded all the images and uploaded them to the forum manually. There are no longer any links to codekinesis.com anymore.
Can you please tell me if the error is still reported, now that the (hopefully) clean files are local and not URLs to an external site?
Can you please tell me if the error is still reported, now that the (hopefully) clean files are local and not URLs to an external site?
I have just got back from holiday and tried that thread again. No problems reported. Unclear what we can deduce from this, except that it is consistent with Jason's suggestion. I am still using XP (please don't all shout at me - AVG still supports XP). Sometime later this year I will be moving on to Ubuntu, as W10 horrifies me.
Thanks to Jason for spending so much time and effort on this.
Thanks to Jason for spending so much time and effort on this.
If you haven't already, you can try the Enterprise editions of W10 for free.
https://www.microsoft.com/en-us/evalcenter/evaluate-windows-10-enterprise
You need an MS account but hey, everyone has got one of those 😉
Just a thought 🙂
https://www.microsoft.com/en-us/evalcenter/evaluate-windows-10-enterprise
You need an MS account but hey, everyone has got one of those 😉
Just a thought 🙂
I am also using XP. A couple of years ago I moved from AVG to Avira. I find it pretty good! Just set it to update once a day rather than every two hours.... I am still using XP (please don't all shout at me - AVG still supports XP). Sometime later this year I will be moving on to Ubuntu, as W10 horrifies me....
You guys seem to have more-or-less solved the issue; I think it was likely an ad with a payload that only revealed itself if the User Agent string indicated Internet Explorer on 32-bit XP.
One thing I would like to add, though, for those using OSX/Safari is that if you turn on the Develop menu*, you can then select from a list of User Agents, so that your system will report another OS/Browser to the website in question. Makes tracking down these kinds of things somewhat easier.
Another option, you could also run the exact OS/Browser in a Virtual Machine (VM) copied from a master VM. You would not be safe from infection ... exactly the opposite, actually ... but you could then delete the (infected) copy of the VM you were running and be on your way.
Naturally you would want to run the guest OS VM on a fully updated version of Windows/OSX/Linux/UNIX to protect against exploits that seek out unpatched systems, such as the one plaguing the British Health System as we speak.
I don't use Network Attached or always-on external drives ... I connect, backup and then disconnect the backup from my active machine when not in use, so I would be safe from the payload in that particular worm which encrypts the backups as well as the infected machine. Plus there is always a week old (or less) unconnected backup of the backup to help should a true disaster occur.
I currently have master VMs for every version of Windows from Win98SE to Win10, 32 and 64-bit versions if that is an option, a BSD UNIX VM, a Linux VM, and a MacOS Server 10.6x VM, so would be happy to help if someone PM's me in case such incidents happen in the future.
* Safari 9.x.x > Preferences > Advanced > √ Show Develop menu in menu bar
One thing I would like to add, though, for those using OSX/Safari is that if you turn on the Develop menu*, you can then select from a list of User Agents, so that your system will report another OS/Browser to the website in question. Makes tracking down these kinds of things somewhat easier.
Another option, you could also run the exact OS/Browser in a Virtual Machine (VM) copied from a master VM. You would not be safe from infection ... exactly the opposite, actually ... but you could then delete the (infected) copy of the VM you were running and be on your way.
Naturally you would want to run the guest OS VM on a fully updated version of Windows/OSX/Linux/UNIX to protect against exploits that seek out unpatched systems, such as the one plaguing the British Health System as we speak.
I don't use Network Attached or always-on external drives ... I connect, backup and then disconnect the backup from my active machine when not in use, so I would be safe from the payload in that particular worm which encrypts the backups as well as the infected machine. Plus there is always a week old (or less) unconnected backup of the backup to help should a true disaster occur.
I currently have master VMs for every version of Windows from Win98SE to Win10, 32 and 64-bit versions if that is an option, a BSD UNIX VM, a Linux VM, and a MacOS Server 10.6x VM, so would be happy to help if someone PM's me in case such incidents happen in the future.
* Safari 9.x.x > Preferences > Advanced > √ Show Develop menu in menu bar
Last edited:
- Status
- Not open for further replies.
- Home
- Site
- Forum Problems & Feedback
- Virus warning from thread pictures